Shao Zhihua, Luo Mingzhu, Zhou Feng
introduction
With the rapid development of a new generation of information and communication technologies and the continuous integration of manufacturing technologies, a new round of industrial change represented by smart manufacturing has emerged throughout the world. The world's major industrialized countries have launched new national strategies for revitalizing manufacturing industries, such as Germany's "Industry 4.0" strategy, the United States' "Advanced Manufacturing" strategy and industrial Internet promotion. In May 2015, the State Council of the People's Republic of China officially issued the programmatic document “Made in China 2025†for manufacturing development, and listed smart manufacturing as one of the five major projects, and it was one of the main directions for the attack. Digitalization, networking, and intelligent development have become the major trends in the development of the future manufacturing industry. This also poses new challenges to the establishment of national and corporate security systems.
First, the relative lag in the development of smart manufacturing related industries in China, and the lack of comprehensive competitiveness, the key products and systems are monopolized by foreign countries and it is difficult to achieve safety and control. Moreover, at present, there is still a lack of systematic research on smart manufacturing security risks. With the official release of “Made in China 2025â€, the domestic smart manufacturing related industries have accelerated their development. However, at present, research on smart manufacturing security risks in China is basically a blank, and there is a lack of awareness and understanding of the security risks of smart manufacturing systems.
Second, the security risks faced by intelligent manufacturing systems are different from the security risks faced by traditional information systems. Different from traditional information systems, intelligent manufacturing systems have different scenarios. In addition, the heterogeneity of heterogeneous network protocols, the diversity of devices, and the security risks of intelligent manufacturing systems are more complicated. There are several factors that have led to an increase in the risk of smart manufacturing systems. For example, the use of standardized protocols and technologies, known security vulnerabilities; connection to other network control systems; insecure and illegal network connections; intelligent manufacturing system related technical information Widespread popularity and so on.
1 The concept of smart manufacturing
Smart manufacturing refers to a new generation of information technology based on the Internet of things, cloud computing, and big data. It runs through all aspects of manufacturing activities such as design, production, management, and service. It has deep information self-awareness, intelligent optimization self-decision, precision control self-execution, etc. The general term for advanced manufacturing processes, systems, and models.
Compared with traditional manufacturing, intelligent manufacturing has its unique connotations and involves four levels of intelligence: The first is the intelligentization of products, and intelligently-manufactured products tend to become smart terminals that can be connected to each other through the Internet of Things. The second is the intelligentization of equipment, which evolves from intelligent manufacturing units, a stand-alone machine, a machine tool, robots to intelligent production lines, intelligent workshops, and intelligent production systems. The intelligence of the third process, the organizational structure of the management, the interaction between the enterprise and the enterprise, how to adapt to the intelligence of the product, and the intelligence of the equipment, need to be reconstructed and adjusted. The fourth is the intelligentization of services. The service-oriented manufacturing industry means that manufacturing companies change the value chain from manufacturing-centered to service-centered in order to gain competitive advantage. Therefore, how to integrate digital technologies, intelligent technologies, ubiquitous network technologies, and new technologies? The integration of information technology into services also requires companies to rethink and plan.
2 Smart Manufacturing 3D Technology System
The essence of smart manufacturing is to achieve vertical integration across different levels of the enterprise equipment layer, control layer, and management layer, horizontal integration across enterprise value networks, and end-to-end integration from the entire product life cycle. Its technical system can build a reference model from the three dimensions of system architecture, product life cycle and value chain. According to the three-dimensional reference model of the intelligent manufacturing technology system, as shown in Figure 1.
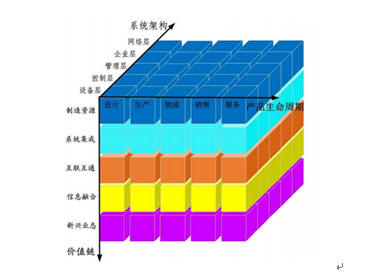
Figure 1 Intelligent Manufacturing 3D System Reference Model
The system architecture dimension is divided into five layers from bottom to top:
(1) The equipment layer includes sensors and instrumentation, barcodes, radio frequency identification, numerical control machine tools, robots and other sensing and execution equipment, as well as on-line non-destructive testing, visual flexible assembly and other intelligent testing and assembly equipment;
(2) The control layer includes Programmable Logic Controller (PLC), data acquisition and monitoring control system (SCADA), distributed control system (DCS), fieldbus control system (FCS), industrial wireless control system (WIA), etc.;
(3) The management team is composed of systems that control the production of workshops/factories, including manufacturing execution systems (MES) and product lifecycle management software (PLM);
(4) The enterprise level consists of enterprise information systems, such as production planning, procurement management, sales management, personnel management, and financial management, to achieve overall management and control of the company's production, mainly including the enterprise resource planning (ERP) system and supply chain management ( SCM) systems and customer relationship management (CRM) systems;
(5) The network layer consists of different companies in the industry chain sharing information through the Internet to achieve collaborative R & D, supporting production, logistics and distribution, manufacturing services.
In the product life cycle dimension, smart manufacturing includes intelligent design, intelligent production, intelligent logistics, intelligent sales and intelligent services. The specific tasks of each link in the intelligent manufacturing system:
(1) The intelligent design link applies intelligent design methods and advanced design information systems to support the intelligent improvement and optimization of all aspects of the enterprise product R&D design process. The systems and technologies involved in smart design are CAD computer-aided design, CAE computer-aided engineering, CAM computer-aided manufacturing, CAPP computer-aided public welfare planning, PDM product data management, networked collaborative design system, and product design knowledge base.
(2) Intelligent production process The intelligent hardware and software technology, control technology and information system are applied to the production process to support the optimal operation of the production process, which is the core of intelligent manufacturing. The systems involved in intelligent production are DNC distributed numerical control technology, FMS flexible manufacturing system, MES manufacturing execution system, and DCS distributed control system.
(3) Smart logistics links include item identification, location tracking, item tracking, and item monitoring.
(4) Smart sales include intelligent enterprise management, intelligent supply chain management, and customer management.
(5) The intelligent service link emphasizes the interconnection of service status/environmental awareness and control, industrial product intelligence services, and manufacturing of the Internet of Things. Including remote maintenance, remote diagnosis, real-time monitoring and so on.
In the dimension of the value chain, the intelligent manufacturing system includes manufacturing resources, system integration, interconnection and interoperability, information integration, and emerging industries, as well as five links. The specific description of each link is as follows:
(1) Manufacturing resources represent physical entities in the real world, such as documents, drawings, equipment, workshops, factories, etc. Personnel can also be an integral part of manufacturing resources.
(2) System integration represents the integration of various manufacturing resources such as raw materials, components, energy, and equipment through two-dimensional code, radio frequency identification, software, and network information technologies. Through the realization of resource integration from small to large, the integration of intelligent equipment/products, intelligent production units, intelligent production lines, digital workshops, smart factories, and even intelligent manufacturing systems can be realized.
(3) Interconnection refers to the use of communication technologies such as local area networks, the Internet, mobile networks, and dedicated lines to realize the connection between manufacturing resources and the connection between manufacturing resources and enterprise management systems.
(4) Information fusion refers to the use of next-generation information technologies such as cloud computing and big data on the basis of system integration and interoperability to achieve information sharing among companies, enterprises, and even more within the premise of ensuring information security. .
(5) Emerging formats include service-oriented manufacturing models such as personalized customization, network collaborative development, industrial cloud services, and e-commerce.
3 Reference Architecture of Intelligent Manufacturing System
The features of smart manufacturing are based on smart factories and digital workshops, with the key manufacturing links being intelligent, and the end-to-end data flow as the foundation and Netcom interconnection as the support. Among them, the intelligent manufacturing of key manufacturing links is the core, which is the intelligentization of manufacturing. Therefore, this paper focuses on the intelligent system of manufacturing, tries to build an intelligent manufacturing system based on the smart factory system architecture, as shown in Figure 2, the five-tier structure, namely, equipment layer, control layer, management, Enterprise and network layers. At the same time, Figure 2 also shows the devices, systems, application software, networks, and related technologies contained in each layer.
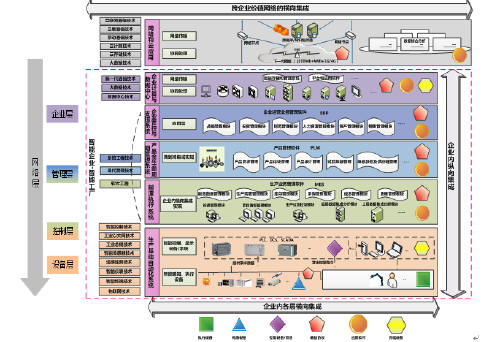
Figure 2 Architecture of Intelligent Manufacturing System (Reference)
The most prominent feature of the intelligent manufacturing system architecture is the three integrated concepts embodied in it, namely, the intelligent manufacturing system's three levels of integration through vertical integration, horizontal integration, and end-to-end integration, to achieve the manufacturing of intelligent.
(1) Vertical integration refers to the collection, processing, communication, and conversion of related data at all levels of the internal system of an enterprise. It stores and expresses information, implements information exchange, process scheduling, and sharing, so that all layers of information security in the system are organically integrated. . The vertical information integration shall ensure that all layers can access the information uploaded by the lower layer and access it through the interface in a standard and extensible manner to realize the application requirement function. The uploaded data must meet the functional requirements of the system and the high-level information can be timely. Accurate to the bottom.
(2) Horizontal integration has two kinds of connotations: 1 Horizontal integration of all internal layers of an enterprise, which establishes a platform for information exchange and sharing for each layer of the intelligent manufacturing architecture, and can be based on the specific conditions of the enterprise. And the data center can also set up distributed computing devices and data storage devices at various levels as required for the construction of corresponding levels of information exchange and sharing platforms. 2 Horizontal integration across enterprise value networks is the formation of data computing and exchange centers between enterprises and enterprises through advanced technologies such as cloud computing, cloud storage, big data, and the Internet. All enterprises improve their own enterprise value chain through the exchange and mining of data.
(3) End-to-end integration refers to the digital integration of end-to-end engineering throughout the entire product value chain, through the establishment of models, the provision of IT support systems, and the construction of a networked end-to-end engineering digital tool chain to achieve product demand analysis and R&D. The information integration of the entire lifecycle of design, manufacturing, sales, and service provides end-to-end support for the entire value chain, making personalized, intelligent product customization possible.
4 Intelligent Manufacturing System Security Risk Analysis
4.1 The concept of intelligent manufacturing system security
(1) Classifying from the perspective of the causes of security problems
The classification of the security of intelligent manufacturing systems from the perspective of the causes of security problems can be divided into three aspects: functional safety, physical security, and information security.
a) Functional safety means that intelligent manufacturing equipment and systems must perform their functions correctly, and when failure or failure occurs, equipment and systems must still be able to maintain safety conditions or enter a safe state; it can be understood as "failure-safety". The concepts closely related to the reliability of equipment and systems.
b) Physical safety is to reduce hazards caused by electric shock, fire, radiation, mechanical hazards, chemical hazards and other factors.
c) Information security can refer to the definition of the information security of industrial control systems in IEC 62443 "Measures taken by the protection system; System state resulting from the establishment and maintenance of protected system measures; Can be exempted from unauthorized access to system resources Unauthorized or accidental change, destruction or damage; based on the capabilities of the computer system, can guarantee that unauthorized personnel and systems can not modify the software and its data, can not access system functions, ensure that authorized personnel are not prevented; prevent the industrial control system Illegal or harmful intrusions, or interference with their correct and planned operations." Intelligent manufacturing system as a key infrastructure, its information security may not only result in the loss of information, but also may cause the failure of the manufacturing process, personnel damage, equipment damage, causing major economic losses, and even cause social and environmental problems.
This article focuses on the analysis of the security risks of intelligent manufacturing systems from the perspective of information security.
(2) Classification from the perspective of safety control
The classification of the security of the intelligent manufacturing system from the perspective of security control can be divided into three aspects: technology, management, and operation and maintenance.
a) Technology, including the application of security products and technologies (such as firewalls, anti-virus software, intrusion detection, encryption technology).
b) Management, including the use of policies, staff training, business planning, non-technical areas based on information security, related to information system security policies and regulations, education, management standards and other aspects.
c) Operation and maintenance mainly includes strengthening mechanisms and methods, correcting operational deficiencies, operating defects caused by various threats, physical access control, backup capabilities, and protection against environmental threats.
4.2 Analysis of Security Risk Factors in Intelligent Manufacturing System
"Risk" is a situation that brings about loss or injury. A measure of risk is a measure of the likelihood of a security incident and the severity of the resulting damage. We should prevent the occurrence of security incidents at all stages of the life cycle such as the demonstration, design, development, integration, operation and maintenance of intelligent manufacturing systems, and we can formulate effective measures to mitigate the impact of the security incidents. Identifying, analyzing, measuring, testing, and evaluating security risk factors are important tools for this work.
It is generally believed that the security risk factors mainly include two aspects: internal and external factors. The occurrence of security events is the result of internal and external factors. For the intelligent manufacturing system, it belongs to the "System of Systems" (System of Systems), that is, a complex system formed by the integration of multiple subsystems through network integration. Therefore, in addition to internal and external factors, the risks between various subsystems should also be considered. Dependency, that is, the coupling effect of the risk factors of each sub-system (fault propagation behavior) on the overall impact of smart manufacturing systems, and even damage. The following will analyze the intelligent manufacturing safety risk factors from three aspects: internal cause, external cause, and fault propagation behavior.
4.2.1 Internal Risks of Security Risks - Vulnerability
Internal causes refer to system internal factors that cause security events in intelligent manufacturing systems. The components of the intelligent manufacturing system can be divided into hardware, software, network structure, control rules and personnel. Therefore, the internal risks of the system mainly come from hardware failures, software defects, network vulnerabilities, imperfect operating rules, and unreasonable system architecture. Insufficient management and human error. These can be collectively referred to as the system's vulnerability. Vulnerability, also known as weakness or vulnerability, is the weak link in assets or asset groups that may be exploited by threats. Damage can be damaged if the vulnerability is used successfully.
4.2.2 Security Risk External Causes - Threats
External factors refer to external factors that cause security incidents in intelligent manufacturing systems. They can be divided into three categories: environmental factors, changes in operating modes, and external attacks.
(1) Environmental factors. Environment refers to all external things (usually called objects) that surround a certain thing (usually called the subject) and have some influence on the thing. It can be divided into natural environment and social environment. Natural environment conditions are an unavoidable and must be considered factor for the product. They refer to the physical, chemical, and biological conditions of the system when it is used, such as climate and environmental conditions, biological environmental conditions, chemical pollutants, mechanical effects, etc. . The environment degrades product performance in all aspects and brings security risks to the system. Social environment refers to the sum of social material and spiritual conditions within the scope of human survival and activities. Changes in the social environment, such as changes in political and economic conditions, can affect people’s lives, affect people’s emotions and behaviors, and lead to the occurrence of human errors; moreover, changes in political, economic, and legal environments can affect smart manufacturing systems. The changes in the functions and structures of the science and technology environment will affect the theory and technology related to the intelligent manufacturing system, which will cause the evolution of the system and lead to the occurrence of security incidents.
(2) Operation mode. Intelligent manufacturing systems need to constantly change the operating mode of the system in order to accomplish different tasks or to make the system safe, economical, and rational. This will cause changes in the system structure or parameters and affect the hardware, software, and network structure of the system. , causing security incidents to occur.
(3) External attacks. An external attack refers to the destruction of hardware and software in the system by people or things outside the system. It can be divided into physical attacks and non-physical attacks. Physical attacks generally refer to human malicious destruction, which refers to direct external damage to the elements of the system. For example, an attack on hardware is to interfere with hardware devices by changing environmental parameters or directly changing hardware parameters. An attack on software is by injecting faults at the software level. Non-physical attacks generally refer to cyber attacks. External attacks are the least controllable of the three types of external causes. In recent years, attack techniques have developed rapidly, causing damage to critical infrastructure and having the greatest impact. Therefore, it was focused on in this study.
4.2.3 Fault propagation behavior - coupling of risk factors
Fault propagation refers to the propagation of faults caused by faults between different entities. The entities involved can be physical devices, data objects, statements, functions, processes, and so on. Since the intelligent manufacturing system is a complex networked system, the security risk factors between subsystems will be coupled due to the role of network connections and the interaction of information and energy, and there is a risk dependency between each other, that is, the failure is caused in the system. Within the spread.
In the operation process of the intelligent manufacturing system, after a function or failure of a certain device or subsystem of the system occurs due to external factors or internal factors, the system may cause the function of other devices or subsystems due to the coupling within the system. Failure or failure, in turn, triggers a chain reaction that ultimately leads to functional failure and failure of the entire system. The fault propagation has the characteristics of complexity: from the long-term time point of view, it shows both disorderly instabilities, orderly periodicity and rhythm, and from short-term time, the dynamic behaviors on multiple time scales are mutual. Intertwined, operating modes and fault changes are complex. The fault of intelligent manufacturing system has both regionality and universality in space. The scope of fault coverage is both predictable and random and catastrophic.
4.3 Smart Manufacturing Security Risk Matrix
Based on the above analysis of the security risk factors, the security risks existing in the manufacturing intelligence system can be divided into levels in the form of a matrix, as shown in Figure 3.
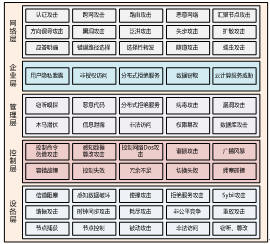
Figure 3 Security Risk Matrix at Each Level of Intelligent Manufacturing System
(1) Network layer: There are security risks such as authentication attacks, cross-network attacks, and route attacks, and there may be security vulnerabilities in network configuration, network hardware, network boundary, and monitoring and recording.
(2) Enterprise layer: There are security risks such as user privacy disclosure and unauthorized access, and there may be security vulnerabilities in the configuration of the enterprise software platform and its hardware.
(3) Management: There are security risks such as snooping, malicious code, and virus/vulnerability attacks, and there may be security vulnerabilities in the management software configuration and its hardware.
(4) Control layer: There are security risks such as control command forgery attacks, network DoS attacks, resonating attacks, and broadcast storms, and there may be security vulnerabilities in the control system.
(5) Device layer: There are security risks such as channel congestion, perceived data destruction, Sybil attacks, and clock synchronization attacks, and there may be security vulnerabilities in the device.
In addition, the five-tier structure of manufacturing intelligence is divided according to functions. From the technical point of view, different levels of components may use the same technology, such as similar operating systems, communication protocols, encryption algorithms, so different levels may exist in the same The risk point.
(1) Among the five levels, there are security risk points such as illegal access, content removal, logical errors, and code defects;
(2) In the three layers of the network layer, enterprise layer, management layer, and control layer, there are often information security risk points such as bus anomaly, eavesdropping and sniffing, password stealing, host vulnerability, virus attack, Trojan latent, backdoor threat, etc.;
(3) In the two layers of the control layer and the equipment layer, there are often security risk points such as random failures and diagnostic errors.
5 Security Protection Recommendations for Intelligent Manufacturing Systems
For the security risks and vulnerabilities faced by various layers of intelligent manufacturing industry, the following information security recommendations can be used. As shown in Figure 4.
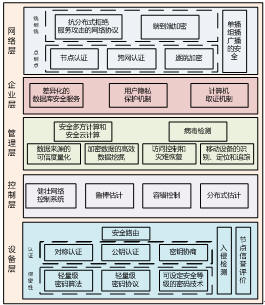
Figure 4 Security Risk Protection Recommendations for Intelligent Manufacturing Systems
(1) Device-level security recommendations: For security risks at the device layer, security routes and industrial firewalls can be deployed to check for intrusions, and device-level nodes can be evaluated for reputation and device registration. The device layer can also perform authentication (including symmetric authentication, public key authentication, key agreement, etc.) and security (lightweight cryptographic algorithms and cryptographic protocols, cryptographic technologies that can set security levels, etc.) Measures to ensure the security of information .
(2) Security recommendations at the control layer: The security risks of the control layer can enhance the robustness and robustness of the network and enhance its fault tolerance.
(3) Management's security protection recommendations: For management's security risks, security multi-party computing and cloud computing, virus detection, trusted metrics of data sources, encrypted data mining, access control and disaster recovery, and access systems can be implemented Mobile devices for identification, location and tracking.
(4) Enterprise-level security protection recommendations: For enterprise-level risks, various database security service measures, user privacy protection mechanisms, and non-repudiation forensics mechanisms for user behavior can be implemented.
(5) Network Layer Security Recommendations: For end-to-end communication security risks, network protocols and end-to-end encryption techniques that are resistant to distributed denial of service attacks can be implemented. For the security risks of network nodes, node authentication, cross-network authentication, and hop-by-hop encryption technology can be implemented. In order to improve the overall confidentiality of information transmission, unicast multicast and broadcast encryption and related security technologies can be implemented.
6 Conclusion
This paper presents a preliminary analysis and analysis of the basic concepts, technical systems, reference architectures, and the security risks involved in the intelligent manufacturing system, and proposes related protection recommendations. With the development of China’s manufacturing industry, the security of smart manufacturing systems is increasingly related to China’s national economy, people’s livelihood, and national security. Research on the safety risks of intelligent manufacturing systems will inevitably increase with the development of “Made in China 2025â€. Concern and research.
banan abanod
Bossgoo(China)Tecgnology.(Bossgoo(China)Tecgnology) , https://www.cn-gangdao.com