1 Introduction Cryptography is often used to protect the intellectual property of digital media, but cryptography protects content only by communication or access control once the data is decrypted or accessed by the user. It is no longer protective, and at the same time the randomness of ciphertext also exposes the importance of information and is likely to attract the attention of attackers. In order to solve these hidden dangers, a new means of property rights protection, digital watermarking and its application in the field of television are proposed here.
This article refers to the address: http://
2 Digital watermarking principle and video digital watermarking features
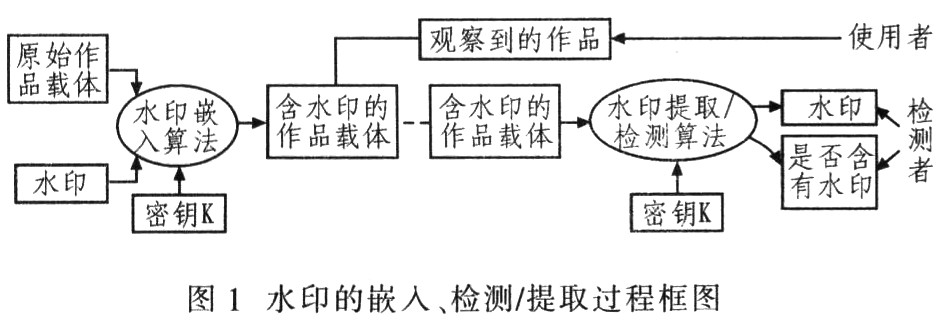
2.1 Principle of digital watermarking A complete digital watermarking system should include three basic parts: watermark generation, embedding and extraction or detection. The watermark embedding algorithm embeds the watermark into the original work carrier by using a symmetric key or a public key to obtain a water-printed work carrier, that is, using the observed work. The watermark detection/extraction algorithm uses the corresponding key to detect or recover the watermark from the watermarked print carrier. Only the detector can use the watermark detection, the extraction algorithm and the key to detect or extract the watermark from the product observed by the user. Since the watermark is transparent, the watermarked work is not easy to attract the attention of an attacker. Figure 1 is a block diagram of the watermark embedding and detection/extraction process.
2.2 Characteristics of video digital watermark The digital watermark embedded in the video carrier is called a video digital watermark. Since the video is composed of a sequence of digital images, the video digital watermark and the digital image watermark have the same characteristics, such as fidelity, robustness, unambiguity, security, reliability, and the like. In addition, video digital watermarking has the characteristics of real-time, blind watermark, random detection, watermark capacity, combination with video coding standards, video rate constancy and low false alarm rate.
3 Main algorithm analysis of video digital watermarking Embedding watermarks in video should generally follow the MPEG coding standard. The main algorithm is analyzed and discussed based on the location of the video watermark embedding.
3.1 Embedding DCT coefficients The watermark is embedded in the DCT coefficients, and the watermark signal is first processed into a random sequence, and then 8×8 DCT is performed. When the watermark is embedded, the DCT coefficients of the watermark are superimposed on the DCT coefficients of the MPEG-2 code stream. But the algorithm needs to consider two issues:
(1) Since the code stream of MPEG-2 is encoded by Variable Length Coding (VLC), the length of the code before and after the watermark is added changes. Therefore, if the length of the video stream is not increased, the watermark appears. When the number of coded bits of the post-DCT coefficient is increased, the original coefficient is retained; (2) In the MPEG-2 coding mode, the inter-coded frame is predicted from other frames, and reconstructed from other frames by using a motion compensation vector. The current frame, the P frame itself may also serve as a predictive reference for other frames, and small changes within a frame will propagate in time and space. Therefore, in addition to the watermark signal, it is necessary to add an offset compensation signal to compensate the watermark signal of the previous frame.
3.2 Embedding motion vectors Embedding watermarks in motion vectors embeds information by modifying the motion vectors of MPEG encoded video streams. The watermark is embedded in the motion vector of the MPEC-4 compressed domain. The algorithm is: obtain the motion vector from the MPEG-4 video stream, calculate the amplitude, select the macroblock with larger amplitude as the embedding position of the watermark, and calculate the macroblock. The phase angle θ of the motion vector determines whether the watermark is embedded in the horizontal or vertical component of the motion vector based on the value of θ. If θ is an acute angle, the watermark is embedded in the horizontal component; if θ is an obtuse angle, the watermark is embedded in the vertical component; if θ is 45°, the watermark is embedded in both the horizontal and vertical components. Assuming that the watermark is embedded in the vertical component V, let b = {0, 1} be the bit value to be embedded, and the embedding rule of the watermark is:

Where T = 2 × <motion estimation search window>, δ = (2n + 1) / q, n is an integer, in general, for a space vector, n = 1; otherwise n = O. q specifies the range of motion vector modification, which is generally 1 or 2. The extraction rule is b = (Vxq + T) mod2.
The algorithm is robust to compression and has a very small impact on the bit rate of the frame. The algorithm only needs simple judgment and addition and subtraction of motion vectors, so the computational complexity is small.
3.3 Embedding facial motion parameters FAP
The watermarking algorithm is embedded in the facial motion parameter FAP (Faeial Animation Parameter). The basic idea is to define a general face in MPEG-4. And can move through the FAP. There are a total of 66 FAPs, including the entire head's motion parameters and local facial motion parameters. The FAP is determined from the video sequence in the encoding process of MPEG-4, which can be regarded as a kmax dimensional vector that changes with time, where kmax is the number of transmitted FAPs (kmax ≤ 66), and t is an integer of the video frame. The time index value, FAPk(t), is the last FAP (k∈{1...kmax}) at time t. The embedding of the watermark is to spread the 1-bit watermark information into more than one FAP, such as the FAP block of MxN. In order to enhance the security and robustness of the watermark, the embedded bit information needs to be extended, modulated, low-pass filtered and amplitude modulated, and finally embedded in the selected FAP block. The detection of the watermark is performed by subtracting the original FAP from the water-imprinted FAP, and then performing the correlation operation with the same random sequence as the watermark embedding, and then judging whether it is greater than a given threshold. When it is greater than, the watermark exists; otherwise, the watermark does not exist. Combining this algorithm with the characteristics of the human visual system can achieve better results.
4 Video digital watermark application in the field of television At present, the application of video digital watermark in the field of television is still rare. However, with the further development of digital TV, the application prospect of this new technology will be very optimistic. The reason is that digital watermarking technology can be applied to many aspects of digital TV platforms.
4.1 The copyright holder of a copyright protection television program may use the key to generate a watermark information for indicating ownership and embed it in the video data of the television program. When the program is pirated or a copyright dispute arises, the copyright owner You can protect your rights by extracting or detecting watermarks. The watermark information of the logo copyright holder can be bundled in the program material at the time of shooting, so that the watermark information is always accompanied by the program material throughout the life cycle. This can be achieved by the device manufacturer adding corresponding functions to the camera, ENG, etc., or when the TV program is released. Add watermark information. Watermarks embedded in digital video can only be erased when the video data is severely corrupted, even if the video quality is degraded, as long as the watermark is valid, it can be identified. The watermark applied to digital TV should be adopted without affecting the picture quality and sound quality of the program. The resulting changes in human visual and auditory are difficult to find, so the video watermark must be invisible, strong and robust, only through special The tools can be extracted and required to be operated in real time. In addition, the algorithm for embedding watermarks should be irreversible. If it is reversible, there are still multiple ownership problems, because the reversible embedding of watermarks allows a malicious attacker to forge a raw data.
4.2 Content Authentication Digital watermarking is used for video content authentication to verify the integrity of video content. In addition to verifying the picture, video and audio also verify timing relationships and continuity. For the temporal characteristics of the video, it may be the frame number in which the frame is embedded in the video in each frame. In this way, if the attack of the single-frame picture content is not considered, it is easy to detect the insertion of other video content, the deletion, exchange of the video frame, and the change of the frame rate. For the content characteristics of the video, the edge information corresponding to the frame picture can be transformed and embedded as a watermark in the picture. At the time of detection, if the content changes, the extracted edge information does not match the edge information embedded in the screen, thereby determining that the content of the portion of the screen has changed. The video program is composed of a video stream and an audio stream. The video feature data can also be embedded into the audio stream as a watermark using an audio watermarking technique, and the audio data feature is also embedded as a watermark in the video stream by using a video watermarking technique to identify the program. Video or audio changes.
4.3 Fingerprint Tracking To avoid unauthorized copying and illegal sales, the copyright owner or publisher embeds different user IDs or serial numbers as different watermarks (fingerprints) into the legal copy of the work and saves them for sale. A database of fingerprints and user identities in the copy, and once the illegal copy is found, the copyright owner or publisher can extract the illegal distributor of the work by extracting the fingerprint. For real-time transmission of video, such as PPV and VOD, different watermarking schemes are required. For PPV (Pay-Per-View), different fingerprint watermarks can be made according to the distribution path, for example, each relay node is embedded with a fingerprint (different watermark); and for VOD, a fingerprint can be made by the server according to different users. Watermark, if the VOD system uses the pre-encryption method to save the video stream on the server, when the user clicks on the video, it may need to decrypt the real-time decryption, add the fingerprint watermark, and then encrypt. In addition, in order to prevent the user from remake, during playback, it may be considered to extract an identification code uniquely identifying the television from the television as fingerprint information embedded in the video.
4.4 Copy Control The illegal copy of the DVD is a fatal blow to the film and television industry. Copy control cannot be implemented using digital watermarking alone, as digital watermarking itself does not prevent illegal copying, it is only part of the data protection system. To prevent illegal copying, you can't do without hardware support. For example, the "interstellar scheme" proposed by companies such as IBM controls the playback, transcription and copying by setting four states to the DVD. The four states are "Copy Free", "One Copy", "No MoreCopy", and "Never Copy". These states are implemented by "Primary Mark" and "Copy Mark" in the embedded video data. Copy-controlled watermarks require very little information to be embedded, but are highly demanding for robustness and security.
4.5 TV program monitoring Manufacturers who advertise on TV stations want to monitor whether a TV channel broadcasts their advertisements on time. Content producers such as TV dramas, movies, MTV, etc. want to know whether the time and number of times the TV station broadcasts its own works exceeds The number of allowed times can be accurately monitored by means of watermarking technology. The information of the identification manufacturer or the manufacturer is used as a watermark signal and embedded in data such as advertisements or TV dramas. The manufacturer or the manufacturer can accurately monitor the number of times, time, and the like of the works by using the watermark monitoring function system (software or hardware).
4.6 Video Audio Delay Automatic Correction Video audio delay correction is simply “matchingâ€. In the production of television programs, video signals and audio signals are usually processed separately. Thus, due to the difference in processing and transmission links, the timing relationship between the video signal and the audio signal changes, and the sound map is out of sync. The above problem can be solved by digital watermarking technology. The feature value is extracted from the audio signal and embedded as a watermark into the synchronized digital video signal. The digital video signal and the audio signal with watermark are normally transmitted and distributed. At the receiving end, the digital watermark (audio feature value) is first extracted from the digital video signal, and compared with the feature value extracted from the received audio signal, thereby finding a corresponding synchronization point. When calculating the delay between the two, the audio delay is controlled to achieve automatic correction of the video audio delay.
4.7 Signal Source Transmission Security Detection In order to ensure the safe broadcast of broadcast television and prevent various types of faults and illegal attacks, the technical quality and program content of the external signal source should be monitored before the external signal is transmitted. With the help of digital watermarking technology, the legitimacy of signal programs can be monitored in the digital domain. For example, to monitor whether a digital satellite signal is illegally transmitted, a watermark can be embedded with a key before the digital television signal is sent to the satellite transponder. After receiving the satellite signal, the key is detected by the key to detect whether there is a watermark. The digital satellite news gathering system is based on synchronous communication satellites. The digital video and audio signal collected at the news site will be transmitted back to the TV news studio. If digital watermarking technology is applied in this system, the live and live broadcast, especially the multi-point live broadcast, can effectively achieve the delay correction of video and audio. Dual function of signal source monitoring.
5 Conclusion According to the characteristics of video, it is pointed out that as a digital watermark of video should meet the requirements, the video digital watermarking algorithm is analyzed and discussed. Finally, for the specific problems of digital TV copyright management, a solution to solve the problem by digital watermarking technology is proposed.
This group is including our new products, such as G9 LED Lamp, LED Refrigerator Lamp, which are very popular in the market. High Lumen G9 LED Lamps widely used in Crystal Lights.Voltage AC220-240V Driverless, used the newest technology AC LED Chip. 230° widely beam angle. G9 led lamp used with Remote Fluorescence Cover. Luminous efficacy more evenly. Maintenance free, easy installation. Low power consumption. Lower heating during operation. More energy saving more efficient. No UV or IR radiation. Saving 90% energy. Welcome all the customers come to inquiry.
New led lamp, G9 LED Lamp, Refrigerator led lamp, Plastic & Aluminum led bulb light, Plastic & Aluminum led flame light, Led Spotlight
Ningbo YiMing Lighting Technology Co., Ltd. , http://www.yimingtech.com